AT&T: Difference between revisions
>CrackRabbit https://raw.github.com/bibanon/Insurgency-Wiki/master/0-/A/T/.26/AT.26T.mediawiki |
>CrackRabbit |
(No difference)
| |
Revision as of 21:17, 12 May 2013
 |
This raid received Media Coverage It may contain anti-semitics, racists, hackers, steroids, and Fox 11 |
 |
- Some random pedophile. |
- Walter Cronkite after God asked what the latest news was. |
- Frost
- /b/
- IRC
- irc.888chan.org #skynet #invasion
- irc.rizon.net #save/b/
- irc.slacknet.org #/b/

July 26, customers report AT&T is blocking access to img.4chan.org (/b/ and /r9k/) except in some parts of Florida, Georgia and Kansas. reddit
UPDATE: AT&T has restored access. stormen.wordpress.com See explanation below.
Moot explains
"Here's what happened:
For the past three weeks, 4chan has been under a constant DDoS attack. We were able to filter this specific type of attack in a fashion that was more or less transparent to the end user.
Unfortunately, as an unintended consequence of the method used, some Internet users received errant traffic from one of our network switches. A handful happened to be AT&T customers.
In response, AT&T filtered all traffic to and from our img.4chan.org IPs (which serve /b/ & /r9k/) for their entire network, instead of only the affected customers. AT&T did not contact us prior to implementing the block. Here is their statement regarding the matter.
In the end, this wasn't a sinister act of censorship, but rather a bit of a mistake and a poorly executed, disproportionate response on AT&T's part. Whoever pulled the trigger on blackholing the site probably didn't anticipate [nor intend] the consequences of doing so.
We're glad to see this short-lived debacle has prompted renewed interest and debate over net neutrality and internet censorship—two very important issues that don't get nearly enough attention—so perhaps this was all just a blessing in disguise." http://status.4chan.org/index.html#2174049422947602936
The Gameplan
We don't want to go all LOL LEGION FREE BOXES TILE SAMPLES on them. That won't solve shit. It'll probably justify it.
Flood the callcenters and inboxes of AT&T. Make them confirm that img.4chan.org (make sure its img.4chan.org and not just 4chan.org) is down. Then make the honest threat of service cancellation if this censorship isn't undone.
FOR IDIOTS WHO DON'T KNOW HOW TO RELOADEVERY: Download Reloadevery. This is a Firefox plugin and can be found here: https://addons.mozilla.org/en-US/firefox/addon/115 Google the following: "AT&T censoring the Internet." Do that in 5 or more tabs, then press the little downwards arrow next to the refresh button. Select Enable every 5 seconds, or every 10 if your computer is slow. This will put AT&T on the Google top 100 and that is where journalists are always looking for news stories on the web. Thus the journalists will put this in the news. BING INSTANT COVERAGE after about 15 mins, google will hit you with some captcha bullshit. Just unlock the 2 captcha codes, and keep reloading.
We also should contact the FCC, (Or whichever federal fuckbody is the people to contact about this kind of censorship. hope its not the fcc. Those guys suck. They fucked up Animaniacs back in the day. Make it more kid friendly, my ass. More like retard friendly. Tone down MY cartoon violence, will you? Add more educational content, WILL YOU!? But that's niether here nor there.)
Also, contact the National Coalition Against Censorship. http://www.ncac.org/
Digg to raise awareness. http://digg.com/tech_news/AT_T_blocks_4chan/
Basically, cause a stink.
the objective of this little operation is to basically make sure that this precedent is not set. Make it absolutely abundantly clear that this is NOT acceptable to Americans and this WILL NOT be allowed to happen, or else face financial and political suicide.
Acting like a retard and trying to DDoS them will only end in them going "MAYBE IT WASNT SO BAD WE CENSORED THESE ROWDY KIDS WITH THE CP AND THE DISGUSTING LANGUAGE"
Fight with what works: this is david and goliath. this is the little man and the big evil corporation. this is the honest consumers fighting back by being consumers: by stop giving them money, by making them look horrible, by causing a PR shitstorm.
Cable companies are already facing economic downturns because people cant afford the massive bills anymore. Make it clear: we can make it SO much worse for them if they keep this shit up.
Here's another tactic: Scaring the sheep. BOO.
Make the people who do use it so afraid of these fucks that they switch to a different provider. This will cause the loss of income, but only a bit. Luckily, every penny adds up and if you get enough people with this, then their stock WILL drop. You can cause this by:
- Getting people to cancel service and change providers. - Flooding the call centers with fake customer service. - Telling Investors/Brokers/Other Stock Pigs to not invest in AT&T.
FIGHT THE POWAH
Block AT&T Back
okay, faggots, listen up.
there has been ONE good solution provided so far. if AT&T censors the internet, the internet censors them.
this is the way it used to work in the good ol' days, before there even was a WWW.
anyone in charge of a router, website, server, or anything at all connected to the internet, start blocking AT&T. When users call you to bitch, tell them that AT&T has decided to start censoring websites. Your users won't know the difference whether it's you or them, but they'll blame AT&T if you tell them to.
Forgive me for not posting instructions or netblocks, but anyone who actually does have this power already knows what to do.
godspeed, gentlemen.
AT&T own:
12.20.0.0/8 76.192.0.0/10 68.88.0.0/13 75.0.0.0/10 99.128.0.0/10
according to ARIN. Hope this helps. Those subnets will block almost all of AT&T.
Edit: updated with more accurate CIDRs.
Edit 2: completed the CIDR set. There are many smaller one-off allocations of /24 /23 and /22 in size, but those 5 appear to be the vast bulk of it.
PHP Script for blocking/redirecting/informing
<?php
function checkATT() {
$ipaddy = $_SERVER['REMOTE_ADDR'];
/*echo $ipaddy;
echo ip_in_range($ipaddy, '12.20.0.0/8');
echo ip_in_range($ipaddy, '76.192.0.0/10');
echo ip_in_range($ipaddy, '68.88.0.0/13');
echo ip_in_range($ipaddy, '75.0.0.0/10');
echo ip_in_range($ipaddy, '99.128.0.0/10'); */
if (ip_in_range($ipaddy, '209.0.0.0/10') ||ip_in_range($ipaddy, '99.128.0.0/10') || ip_in_range($ipaddy, '75.0.0.0/10') || ip_in_range($ipaddy, '68.88.0.0/13') || ip_in_range($ipaddy, '76.192.0.0/10') || ip_in_range($ipaddy, '12.20.0.0/8')) {
echo 'Link to informative article or redirect to same.';
} else {
echo '<!-- Probably nothing here, to not bother non-ATT customers. -->';
}
}
/*
* ip_in_range.php - Function to determine if an IP is located in a
* specific range as specified via several alternative
* formats.
*
* Network ranges can be specified as:
* 1. Wildcard format: 1.2.3.*
* 2. CIDR format: 1.2.3/24 OR 1.2.3.4/255.255.255.0
* 3. Start-End IP format: 1.2.3.0-1.2.3.255
*
* Return value BOOLEAN : ip_in_range($ip, $range);
*
* Copyright 2008: Paul Gregg <pgregg@pgregg.com>
* 10 January 2008
* Version: 1.2
*
* Source website: http://www.pgregg.com/projects/php/ip_in_range/
* Version 1.2
*
* This software is Donationware - if you feel you have benefited from
* the use of this tool then please consider a donation. The value of
* which is entirely left up to your discretion.
* http://www.pgregg.com/donate/
*
* Please do not remove this header, or source attribution from this file.
*/
// decbin32
// In order to simplify working with IP addresses (in binary) and their
// netmasks, it is easier to ensure that the binary strings are padded
// with zeros out to 32 characters - IP addresses are 32 bit numbers
Function decbin32 ($dec) {
return sprintf('%032b', $dec);
}
// ip_in_range
// This function takes 2 arguments, an IP address and a "range" in several
// different formats.
// Network ranges can be specified as:
// 1. Wildcard format: 1.2.3.*
// 2. CIDR format: 1.2.3/24 OR 1.2.3.4/255.255.255.0
// 3. Start-End IP format: 1.2.3.0-1.2.3.255
// The function will return true if the supplied IP is within the range.
// Note little validation is done on the range inputs - it expects you to
// use one of the above 3 formats.
Function ip_in_range($ip, $range) {
if (strpos($range, '/') !== false) {
// $range is in IP/NETMASK format
list($range, $netmask) = explode('/', $range, 2);
if (strpos($netmask, '.') !== false) {
// $netmask is a 255.255.0.0 format
$netmask = str_replace('*', '0', $netmask);
$netmask_dec = ip2long($netmask);
return (ip2long($ip) & $netmask_dec) == (ip2long($range) & $netmask_dec);
} else {
// $netmask is a CIDR size block
// fix the range argument
$x = explode('.', $range);
array_pad($x, 4, '0');
list($a,$b,$c,$d) = $x;
$range = sprintf("%u.%u.%u.%u", empty($a)?'0':$a, empty($b)?'0':$b,empty($c)?'0':$c,empty($d)?'0':$d);
$range_dec = ip2long($range);
$ip_dec = ip2long($ip);
# Strategy 1 - Create the netmask with 'netmask' 1s and then fill it to 32 with 0s
#$netmask_dec = bindec(str_repeat('1', $netmask) . str_repeat('0', 32-$netmask));
# Strategy 2 - Use math to create it
$wildcard_dec = (1 << (32-$netmask)) - 1;
$netmask_dec = ~ $wildcard_dec;
return ($ip_dec & $netmask_dec) == ($range_dec & $netmask_dec);
}
} else {
// range might be 255.255.*.* or 1.2.3.0-1.2.3.255
if (strpos($range, '*') !==false) { // a.b.*.* format
// Just convert to A-B format by setting * to 0 for A and 255 for B
$lower = str_replace('*', '0', $range);
$upper = str_replace('*', '255', $range);
$range = "$lower-$upper";
}
if (strpos($range, '-')!==false) { // A-B format
list($lower, $upper) = explode('-', $range, 2);
$lower_dec = (float)sprintf("%u",ip2long($lower));
$upper_dec = (float)sprintf("%u",ip2long($upper));
$ip_dec = (float)sprintf("%u",ip2long($ip));
return ($ip_dec>=$lower_dec) && ($ip_dec<=$upper_dec);
}
echo 'Range argument is not in 1.2.3.4/24 or 1.2.3.4/255.255.255.0 format';
return false;
}
}
checkATT();
Let the rest of the world know
Google bomb the story.
while [ true ] ; do curl "http://www.google.com/search?q=att%20internet%20censorship" -A "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)" > /dev/null ; done
AnonTalk Is To Blame
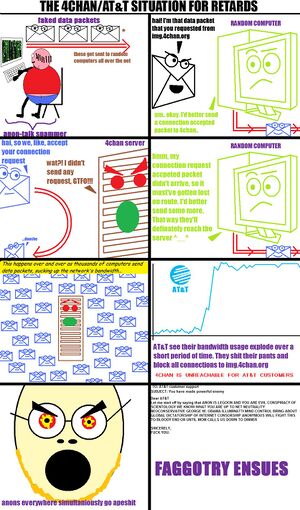
It has been speculated by Fox News [1] that the obvious cause behind all this trouble is Kimmo Alm, owner of anontalk.com, who has since 2007 been waging a war against 4chan via spam and DDoS, but starting summer 2009, has been encouraging his user base to write lots of false reports in about 4chan. Kimmo also considers /b/ and /r9k/ to be AnonTalk's main competition.
Going by AT&T's statement, one of these things happened:
- Kimmo has succeeded in getting his pedosheep userbase to send lots of false complaints to AT&T, Cogent Communications, and others. According to AT&T's July 27, 2009 press release [2] it was a single AT&T customer getting DDoS'd so for each ISP that blocked 4chan, it could have been a single pedo making complaints.
- Kimmo has been spoofing img.4chan.org's IP addresses to DDoS random people. AT&T, Cogent, and Comcast each have gotten something like 887,000 incoming requests from someone spoofing that IP so far and climbing. In addition, when he does DDoS, he uses botnets going through the major ISPs as well.
- Kimmo has been filling /b/ with child pornography and this was why AT&T decided to block it.
Technical Details of Blocking /b/
AT&T is employing a technique called BGP black holes to kill access to 4chan.
4chan is hosted on 207.126.64.181 and 207.126.64.182 and ATT is originating more specific routes to their network than the regular announcement of 207.126.64.0/24 that is normally used. Because BGP is a longest match routing protocol, anything more specific than the /24 will be used.
This can be seen from AS 7132 (legacy SBC Global) by telnetting to route-server.sbcglobal.net and running the command 'show route 207.126.64.181 detail'
One of the entries is:
*BGP Preference: 170/-2001 Next-hop reference count: 1312 Source: 151.164.0.122 Next hop: 66.159.184.161 via fxp0.0, selected Protocol next hop: 192.0.2.1 Indirect next hop: 889c7f8 131180 State: <Active Int Ext> Local AS: 7132 Peer AS: 7132 Age: 2d 10:48:52 Metric: 0 Metric2: 0 Task: BGP_7132.151.164.0.122+179 Announcement bits (2): 0-KRT 2-Resolve tree 1 AS path: I (Originator) Cluster list: 151.164.0.122 AS path: Originator ID: 151.164.0.131 Communities: 7132:666 7132:9999 no-export Localpref: 2000
As seen is the community of 7132:666 (best practice is to use use 666 as your BGP blackholing community). Along with that is no-export which keeps that route announcement local only to ATT. The most important entry is
AS path: Originator ID: 151.164.0.131
That is adm5-l0.rcsntx.sbcglobal.net which is an administrative router loopback address in Texas that is originating the blackhole to the rest of the ATT network. Without that router injecting the route, there will be no block.
That is basically how they're blocking it nationally. Only addresses on the AS 7132 network seem to be affected.
Attention
Don't try to DDoS or do ANYTHING illegal or legally ambiguous to AT&T. This is a corporation with more resources, manpower, and preparation than anything you script kiddies have ever dealt with. You will be caught and prosecuted. Go through legal channels and reverse this using legitimate means.
Geography
List of cities and localities that are rumored to be experiencing full or partial blocking
- Much of Southern California
- Los Angeles, CA
- Santa Cruz, CA
- SF Bay Area, CA
- Detroit, MI (Confirmed)
- Tyler, TX
- Houston, TX
- Oklahoma City, OK
- Dayton, OH
- Toledo, OH
- Chicago, IL (Confirmed)
- San Antonio, TX
- several cities in CT
- Sacramento, Ca
- St.Louis, MO
AT&T wireless services, including laptop cards and iPhones, are not affected as of 7-26-2009 4:49PM PDT.
AT&T Contact Information
AT&T NOC (Network Operations Center)
+1-214-286-5193
Customers are not supposed to call this number. This number is secret and AT&T does not want to spread it. That is why you should spread this number.
AT&T Residential Service
Customer Service Available weekdays from 7 am to 9 pm and Saturday from 8 am to 5 pm.
Service Center:
1-800-288-2020
Disconnect or transfer service:
1-800-288-2020
All other contact information concerning services can be found here.
Phone numbers
Fax:
- 1-800-310-8129
- (314) 331-9896
- 1-800-443-4757
- 1-847-671-8705
- 1-214-761-8275
- 1-678-893-1181
- 1-908-532-1395
- 1-888-308-7186
- 1-678-893-1181
- 1-908-532-1395
- 1-404-829-6310
- 1-800-325-1479
- 1-704-547-8885
- 1-678-893-1181
- 1-925-824-0108
- 1-214-576-4439
- 1-907-777-2423
Phone:
- 1-800-400-1447
- (210) 821-4105
- 1-800-759-8195
- 1-866-879-9476
- 1-214-576-4413
- 1-678-893-1200
- 1-877-272-2544
- 1-877-444-6944
- 1-678-893-1200
- 1-866-336-8278
- 1-800-325-1480
- 1-540-983-6233
- 1-800-228-3751
E-mail (don't spam these k? lol):
- aborling@attnews.us
- abuse@sbcglobal.net
- agrundma@attnews.us
- alexa.kaufman@att.com
- analyst@att.com
- andrew.morgan.1@att.com
- ashaw@attnews.us
- bbrokowski@attnews.us
- bburgess@attnews.us
- bdwyer@attnews.us
- billing@att-webhosting.com
- bwestric@attnews.us
- cbauer@attnews.us
- cbirch@attnews.us
- cbylund@attnews.us
- ccomes@attnews.us
- copyright@sbis.sbc.com
- cpendleton@attnews.us
- cssupport@att-webhosting.com
- dcutin@attnews.us
- domreg@att-webhosting.com
- dvarghese@attnews.us
- ehs@att.com
- gbrutus@attnews.us
- hriefs@attnews.us
- info@sbcsuppliers.com
- jbart@attnews.us
- jbridges@attnews.us
- jcarrach@attnews.us
- jessica.garcia@sbc.com
- jhillery@attnews.us
- jkearney@attnews.us
- joe.chandler@att.com
- john.britton@att.com
- jrountree@attnews.us
- jtaber@attnews.us
- kate.mackinnon@att.com
- kkowalsk@attnews.us
- lferguson@vfw.org
- lw1501@att.com
- mark.a.siegel@att.com
- mbutler@attnews.us
- mcoe@attnews.us
- mgiller@attnews.us
- michael.balmoris@att.com
- mroskopf@attnews.us
- nabauer@attnews.us
- ncollins@attnews.us
- nhickey@attnews.us
- fox@attnews.us
- sales@att-webhosting.com
- Sarah.harsh@att.com
- sbean@attnews.us
- smccain@attnews.us
- sphillips@attnews.us
- stsmith@attnews.us
- support@att-webhosting.com
- support@attwifi.com
- homas.hopkins@att.com
- troopsupport@attnews.us
- uplink@vfw.org
- vastros@attnews.us
- vsmith@attnews.us
- walt.sharp@att.com
- wfuller@attnews.us
- wwarnock@attnews.us
- wyles@att.com
- att@computershare.com
- drucilla.cessac@att.com
- jennifer.ousley@att.com
- brooks.mccorcle@att.com
- kent.evans@att.com
- jeff.fancher@att.com
- william.kuhn@att.com
- joseph.parsons@att.com
- jerrell.k.ross@att.com
- derek.roy@att.com
- christopher.womack@att.com
- privacypolicy@ATT.com
Extracurricular Activities
AT&T CEO contact info:
Randall Stephenson, AT&T CEO
rs2982@att.com (direct)
randall.stephenson@att.com
phone: 210-351-5401 (direct to his secretary)
fax 210-351-3553
alternate phone: 210-821-4105 (headquarters, press 3, ask for Mr. Stephenson's office)
175 E. Houston
San Antonio, TX 78205
Have a chat to some investors about who they associate with here
Victories
Story on AT&T's censorship is the Top in 24 Hours and Top in All Topics of Digg as of 7/26/09.
Story on AT&T's censorship get's slashdoted and reaches frontpage as of 7/26/09.